Cybercrime has evolved. Gone are the days when hackers relied solely on complex code. Today, the battlefield is psychology — your instincts, trust, and curiosity. In 2025, the most sophisticated hack often starts not with technology, but with human behavior.
Hacked by Fear, Curiosity, and Urgency
Think back to the last time you clicked a link, downloaded an attachment, or responded to a message without thinking. Chances are, you’ve already been a target—even if you didn’t know it. Social engineering is the art of manipulating people to give away sensitive information or take unsafe actions.
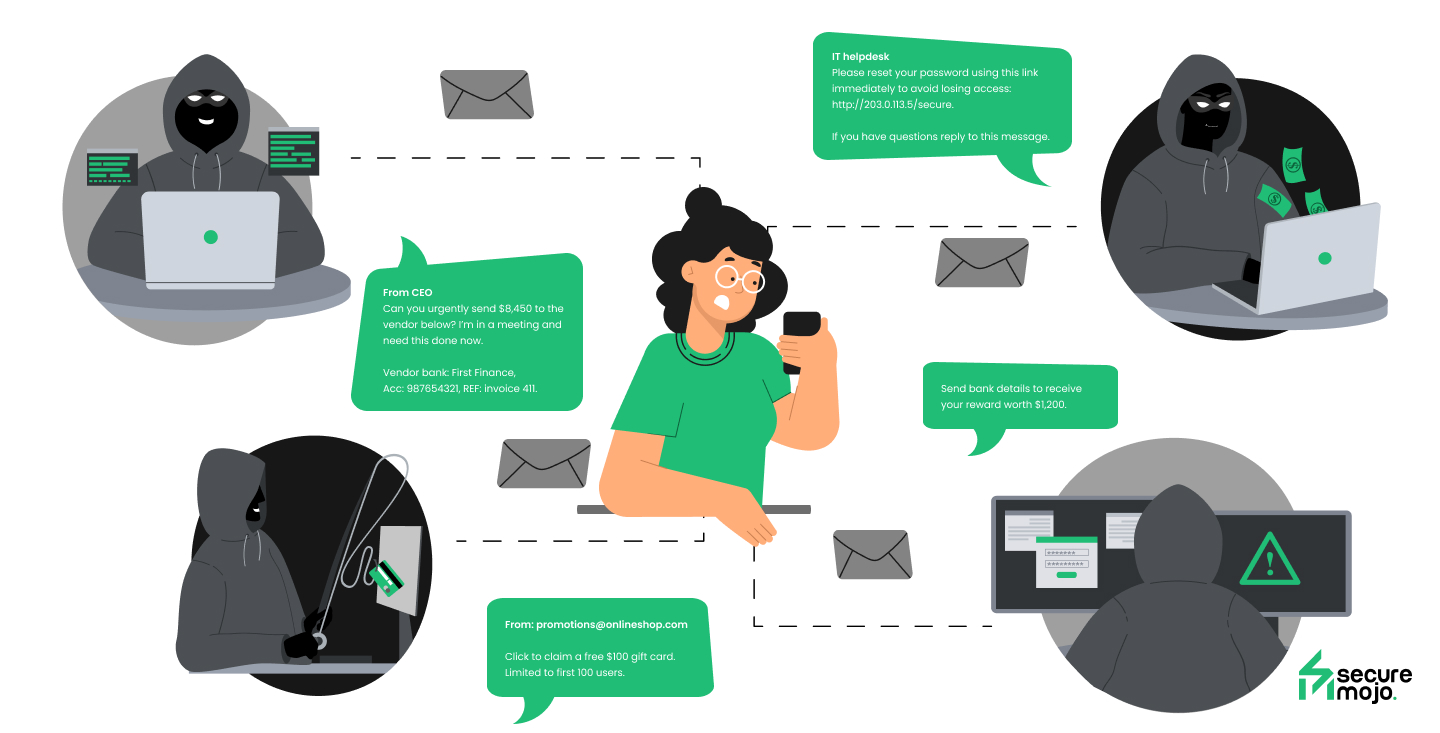
Fear, urgency, and curiosity are their most powerful tools. For example, a simple message threatening your account with suspension can make you act before you think. Or a notification claiming that you’re missing out on an opportunity might trigger you to click without verifying. These tactics aren’t random — they’re carefully designed to exploit the way humans react instinctively.Even experienced professionals can fall victim to these psychological traps. It’s a reminder that cybersecurity isn’t just about software; it’s about being aware of how our own instincts can be exploited.
These aren’t gimmicks. They’re carefully engineered triggers designed to bypass logic and hijack instinct. Humans are the weakest, yet most predictable, link in the digital chain.
Deepfakes and AI: When Reality Is Optional
Technology has blurred the line between what’s real and what’s fabricated. AI-generated voices, deepfake videos, and hyper-realistic impersonations are no longer sci-fi concepts—they’re real threats appearing in offices and homes worldwide.
Imagine this: you receive a call from your CEO. Their voice sounds familiar, their words urgent. They ask you to transfer funds immediately. Trusting the voice, you comply. Only later, you discover it wasn’t them at all.
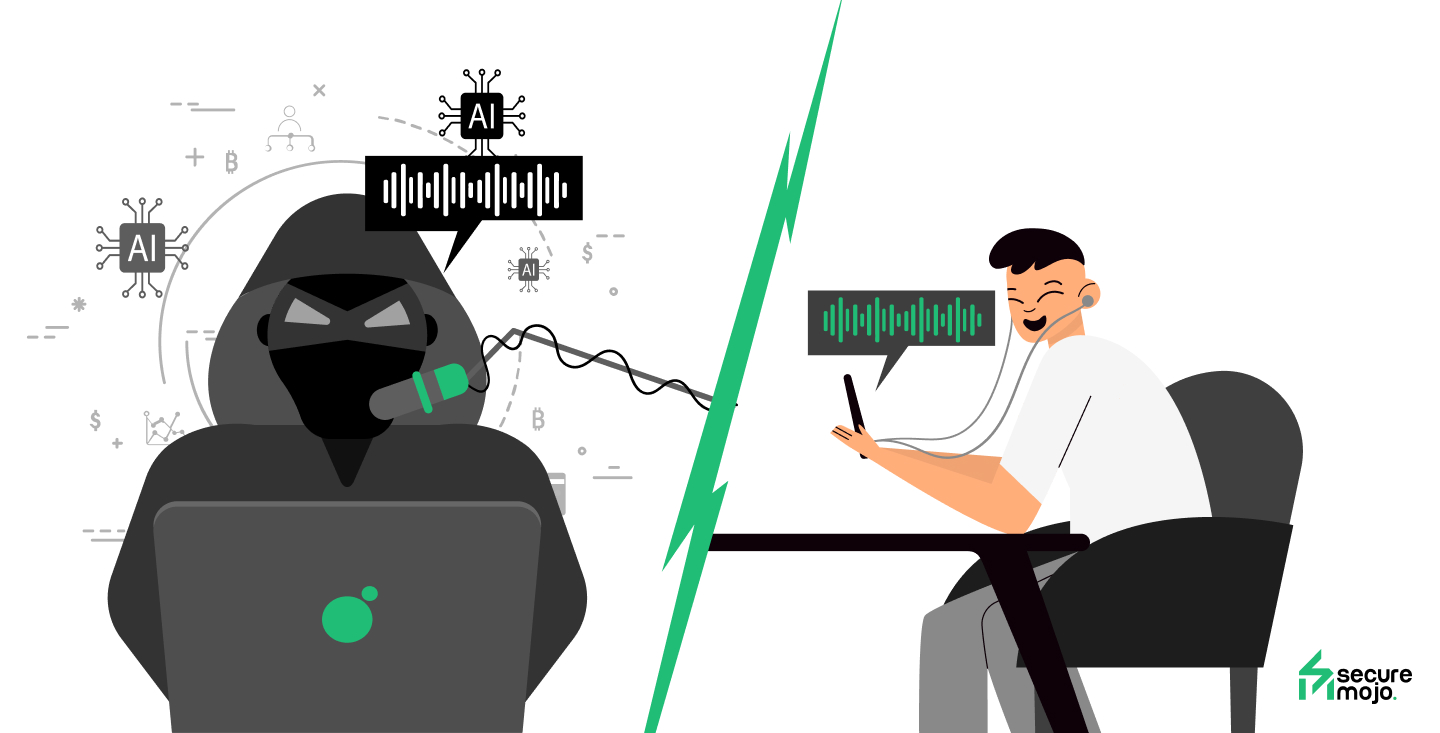
This is the new reality. Hackers now exploit trust itself, creating illusions so convincing that even our instincts struggle to distinguish truth from fiction. Awareness and verification are the only reliable defenses in a world where reality can be manipulated with a click.
Everyday Actions, Extraordinary Risks
Cyber breaches aren’t reserved for the tech-savvy or corporate elite. Ordinary actions often open doors to extraordinary risks:
- Reusing passwords across multiple accounts
- Sharing sensitive information casually in chats or emails
- Clicking links without verifying sources
- Using unsecured networks for personal or financial tasks
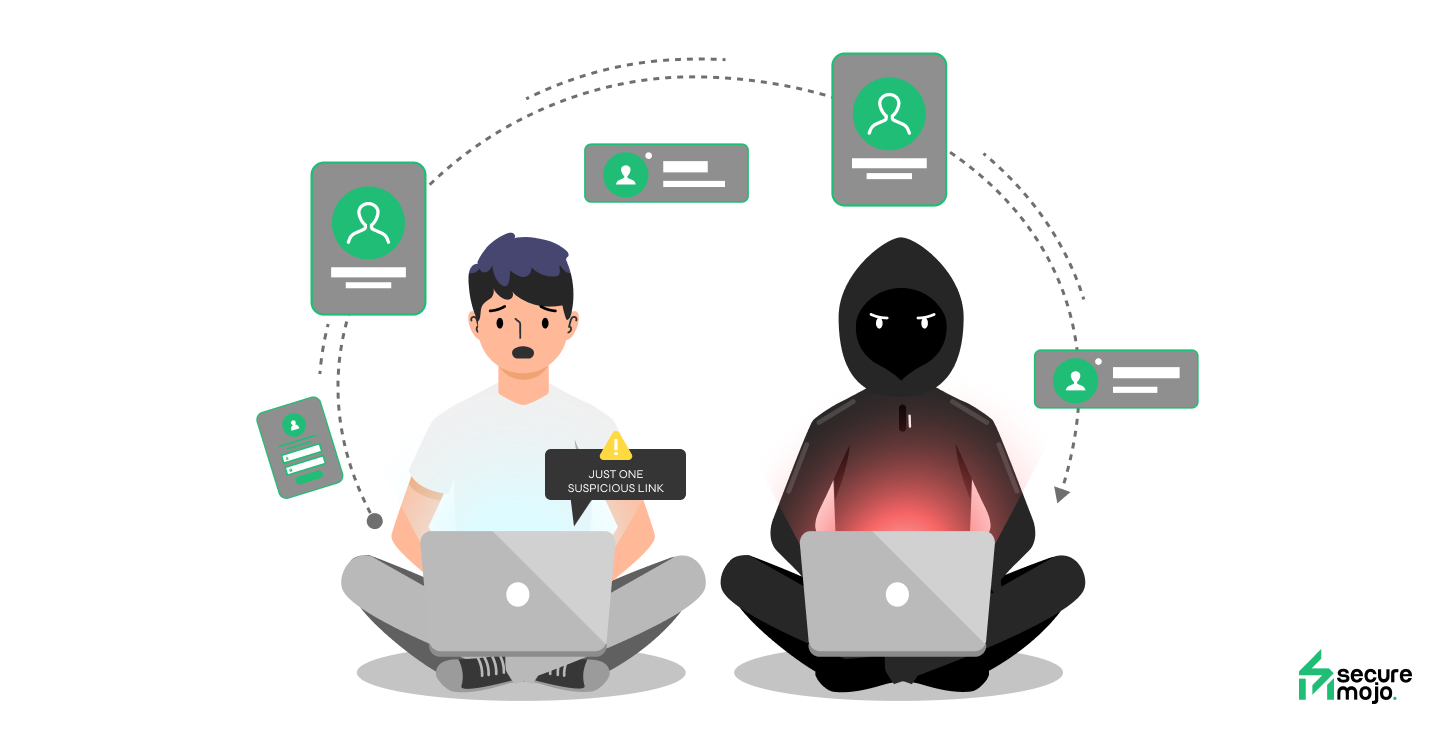
Even clicking a link without verifying the source can lead to phishing attacks or credential theft. These small actions, repeated across millions of users, create massive opportunities for hackers. The lesson is clear: your day-to-day behavior is the first line of defense — and your awareness is the most powerful weapon.
The Human Firewall
Technology can only protect you so far. In a landscape dominated by deception, the real firewall is human awareness. Pausing before clicking, verifying requests, and using multi-factor authentication are small actions that make a huge difference.
Learning from real-world examples also sharpens intuition. Each story of someone falling victim to a scam teaches a lesson that software cannot: how humans think, react, and make mistakes. At Secure Mojo, we believe that cybersecurity begins in the mind, not just the machine. Awareness evolves, and it’s timeless.
Redefining Security: From Fear to Empowerment
Here’s the truth: we’ve all been hacked — by our impulses, our trust, and our curiosity. But that doesn’t mean we’re powerless. Every click, every decision, every moment of pause is a chance to reclaim control. Cybersecurity isn’t about walls, firewalls, or endless software updates alone — it’s about awareness, instincts, and informed choices.
Imagine a world where you move online with confidence, where messages don’t trigger panic, and links don’t demand blind trust. That world is possible — and it starts with small, conscious actions. Verifying a request, thinking before clicking, questioning a “too good to be true” offer — these may seem simple, but they create a human firewall no hacker can bypass.

At Secure Mojo, we believe that knowledge isn’t just power — it’s freedom. Freedom from fear, from manipulation, and from the feeling that the digital world is out to trick you. By learning, observing, and staying aware, you can navigate the digital landscape not as a potential victim, but as a confident, empowered user.
Cybersecurity is no longer just a technical challenge — it’s a human challenge, and human ingenuity is our best defense. So the next time a message seems urgent, a link seems tempting, or a voice seems familiar, pause, question, and act consciously. That pause is your superpower.
Because in a world full of deception, awareness is not just protection — it’s mastery. And mastery is yours to claim.
Found this article interesting? Follow us on Twitter , LinkedIn and also on our Website to read more exclusive content we post.